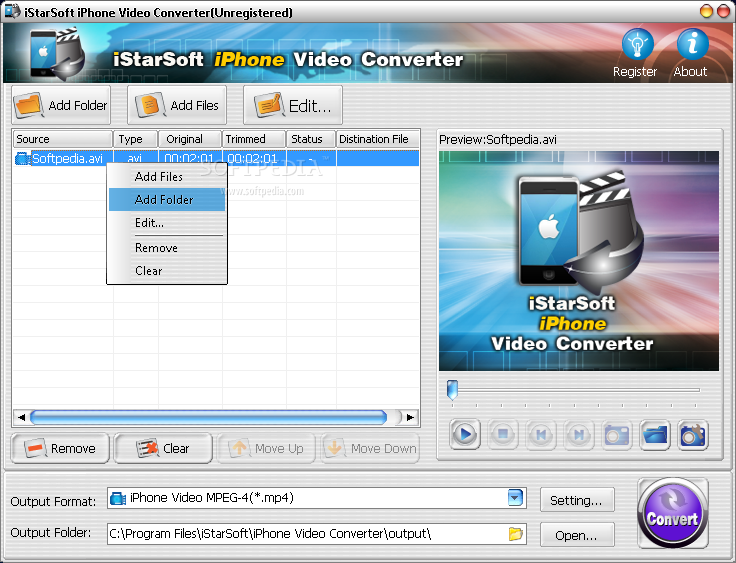
The iStarSoft iPhone Video Converter application will help you convert video to iPhone formats including AVI, MPEG, WMV, MOV, MP4, VOB, XviD, WMA, ASF, 3GP, MP3, M4A to iPhone.It also lets you set encoding parameters including resolution, bit rate, frame rate, aspect ratio to get the best video quality. And of course, you can also choose to use the default settings.With its user-friendly interface, you can easily finish the conversion with just a few clicks of your mouse.Support Input Video Formats:AVI, AVM, ASF, WMV, AVS, FLV, MKV, MOV, 3GP, MP4, MPG, MPEG, DAT, OGM, VOB, RM, RMVB, TS, TP, IFO, NSVConvert any video / audio format to iPhone & iPhone 3G